TrueCrypt for Mac By TrueCrypt Foundation Free Editors' Rating Download.com has removed the direct-download link and offers this page for informational purposes only. However, TrueCrypt is a bit insecure for the mounted device for those reasons discussed before. However, if you are thinking to download TrueCrypt software now, then it could be risky and problematic. This is because it has been officially stopped from being offered and is not available for download since 2014.
It supports on-the-fly Download truecrypt mac, truecrypt mac, truecrypt mac download free. Posted by Tim to BitLocker for Mac Tips on March 9th, 2017Truecrypt 7 1a Download CnetTruecrypt 64 Bit MacDownload Truecrypt For MacTrueCrypt for MacTrueCrypt was a free and open-source disk encryption utility first launched in 2004. Download the latest version of TrueCrypt for Mac for free. Read 29 user reviews and compare with similar apps on MacUpdate.
| Why? | Install it | Volumes | Use it |
|---|
TrueCrypt is a free and open-source program designed to secure user data by using encryption (crypto) and stegonagraphy (stego). The true-crypt program is freely available for download from the 'sourceforge' web-site for Windows 2000/XP/Vista and Linux. Sorry Mac users, you will have to wait until sometime in Q1 2008... The examples and screen-shot detailed here will cover an installation of TrueCrypt version 4.3 on Windows XP Professional Service Pack 2.
Obtaining TrueCrypt...
Truecrypt Download Mac
Simply save the zipped folder and then extract the contents prior to install.
Why bother?
The data stored on your hard drive is your own property, you are responsible for it's integrity. However in many computing environments, such as corporate networks and public kiosks data is considered the property of facilitating party. For example, e-mail messages on a corporate e-mail server are legally considered the property of that company as are the documents and data stored on corporate file servers. I try to keep a very large separation between personal data and work-related data. Personal content of any kind does not belong on a corporate computer. At least ,that is what any IT or security officer would tell a user after data has been confiscated. That idea may be a sensible approach, but given the amount of time a user is spending at work, the rule is far from practical. Personal data and professional data is bound to be mixed on a computer's hard drive at any given time. It is still your responsibility to protect and control your data, and truecrypt can assure that prospect.
Portable computing environments add another variable to data security. Laptops are often stolen and portable USB flash-drives are misplaced and left behind. TrueCrypt can be used to secure an entire flash-drive as well as contents on a laptop's hard drive. I have found numerous flash-drives in the labs around campus and even in some classrooms. All of these drives contained numerous items of personal data, but strangely not all of them had a file described how to contact the owner. Identity theft is a very common crime and can be easily facilitated by unsecured personal data found on lost or stolen devices.
Installing TrueCrypt...
TrueCrypt must be installed by an account with administrative privileges, but it can be used by any user account on the computer. The program downloads as a zipped folder archive. The Windows XP compressed folder utility can be used to extract the program to an uncompressed directory. The install cannot happen from within the compressed folder.
Double-click the setup executable (TrueCrypt Setup) to get started. The default options are smore than suitable for a first-time install.
Depending on the speed of your computer's CPU and the amount of installed RAM, TrueCrypt should install in a matter of minutes. There is no reboot required at the end to finalize the installation.
TrueCrypt is now installed, but it is not actually protecting anything yet. An encrypted volume must be created and configure to allow the storage of data that should be secured. TrueCrypt hides protected data in plain sight as a normal file, that a normal file scan would over look. A bit of trickery is involved in this process to make your TrueCrypt volume look like nothing particular. The encrypted volume is mounted and accessed by using the TrueCrypt program, otherwise the volume is just another file. A beginner's web-page is made available for first-time users to review prior to continuing.
Download Truecrypt Software
Creating a TrueCrypt volume...
Click the 'Create Volume', button to start the wizard. A standard volume will work just fine. If you wear a tin-foil hat, then a hidden TrueCrypt volume is what you need. Click 'Next >'
The next step would be to select a file location or device for the volume. Choose 'Select File...' to navigate to a place on the files system and create the TrueCrypt volume. Choose 'Select Device...' to navigate to a USB flash drive that will be formatted as a TrueCrypt volume. Any data currently on USB flash drive will be removed as a result of this process.
In this example I am going to make a TrueCrypt volume in the 'My Documents' folder called 'homedir.bkf'. The .bkf extension is the same used by the Windows 'NTBackup' utility. My TrueCrypt volume will masquerade on the hard disk as a backup file and if NTBackup were to try and mount the file, it would come up as invalid. Type any file name and extension you choose and click 'Save'.
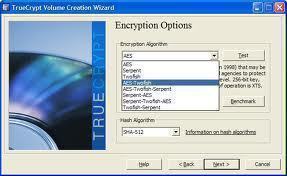
What type of hashing algorithm and encryption scheme is the next choice to make. There are numerous choices available for both of these options. Feel free to look through them all and the descriptions. The defaults are 'AES' for the encrypting algorithm and 'RIPEMD-160' for the hashing duties. AES' job is to secure the data inside a 256-bit shell on the volume's unique file system. RIPEMD-160 hashes the data and produces a unique digital finger print for validity and integrity purposes. Click 'Next >'.
How big do we want the TrueCrypt volume to be? My example of a backup file gives some pretty decent leverage regarding size. If permitted, TrueCrypt will use all remaining space on the HDD. That will not be a good idea. In order to function properly, Windows XP needs around 15% free HDD space at any given time. I will make volume 120 megabytes (MB) in size. Click 'Next >'.
The next step is to provide a password to lock/unlock the TrueCrypt volume. This step is extremely important for two reasons. First, the password needs to be a unique and complex password or pass-phrase. Do not use any of the common password that you may use on other systems. I would go with the pass-phrase option instead of a password. A pass-phrase is a sentence or sentence fragment used in place of a single word. The advantage is length and complexity of a traditional word. The longer a password/pass-phrase is, the longer it will take to crack. Values encrypted with AES will take decades to crack with modern technology. As the image below illustrates, I provided any insanely long pass-phrase. The second reason is any loss of the password will render the secured data unrecoverable. DO NOT FORGET the password, and be sure to make a backup of all encrypted data.

TrueCrypt will then format the volume and created a set of keys used by AES to encrypt/decrypt the volume whenever it is accessed. Any file system will do. I just would not use 'FAT' for volumes over 2048MB (2GB) in size. 2GB is the functional limit for FAT. Volumes larger than that can use NTFS or other files systems. Click 'Format' to proceed.
A prompt will notify you when the volume has been properly formatted. Click 'OK' to continue.
The volume creation process is now complete. A file has been created in the location specified under the conditions indicated in the wizard.
Using TrueCrypt...
Before a TrueCrypt volume can store data inside of it, the volume must opened and mounted. To do so, open the volume's file from the TrueCrypt program by clicking the 'Select File...' button.
Select the TrueCrypt volume from the 'Select a TrueCrypt Volume' dialog box. The default is to check in the user's 'My Documents' folder.

Once that is done, click the 'Mount' button to open the volume under a drive letter.
TrueCrypt will prompt for a password, enter it and the volume will be mounted like a separate partition on your computer.
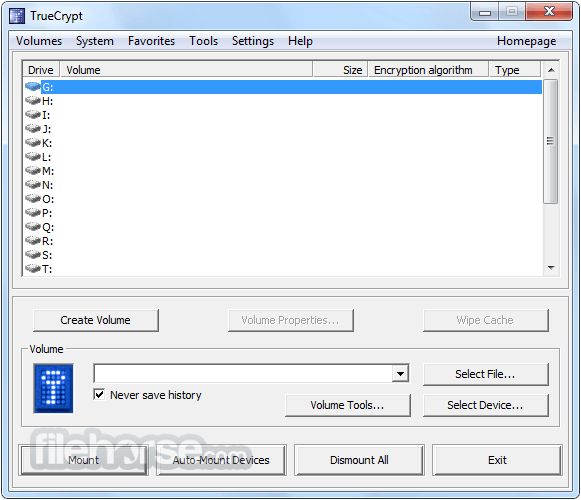
The mounted drive as show from within TrueCrypt.
... and from within Windows Explorer, shown as 'Local Disk (T:)'
Data can be added/removed from the volume while it is mounted like it was a USB flash-drive, floppy disk, or even Zip drive. All data placed onto the volume is encrypted once the volume is dismounted. When finished using the volume, dismount it by selecting the dismount command from within the TrueCrypt menu in the task-bar. The menu can be accessed by right-clicking the TrueCrypt icon in task-bar
Jason Watkins, 12/31/2007